Ubuntu comes with ufw (uncomplicated firewall) installed by default. This is a frontend for iptables/nftables, the built-in Linux firewall, and is meant to make firewall management a bit easier.
In this guide, you’ll see how to add rules to the firewall to open ports and allow certain services to have access through the firewall on Ubuntu.
Allow Port Through Ubuntu Firewall
1. To allow a certain port through the firewall, use the following command syntax. In this example, we’ll allow TCP port 22 (SSH) through the firewall.
$ sudo ufw allow 22/tcp
2. In case you need to allow TCP and UDP packets through the firewall, just specify the port number in your command.
$ sudo ufw allow 53
3. Make sure you have ufw enabled in order for any of these changes to take effect.
$ sudo ufw enable
4. And then check your configured rules.
$ sudo ufw status Status: active To Action From -- ------ ---- 22/tcp ALLOW Anywhere 53 ALLOW Anywhere 22/tcp (v6) ALLOW Anywhere (v6) 53 (v6) ALLOW Anywhere (v6)
See below for commands that will allow common ports and services through Ubuntu’s ufw firewall.
Allow SSH (port 22)
$ sudo ufw allow ssh
Allow HTTP (port 80)
$ sudo ufw allow http
Allow HTTPS (port 443)
$ sudo ufw allow https
Allow Apache or NGINX Web Servers
$ sudo ufw allow "Apache Full" $ sudo ufw allow "NGINX Full"
Allow FTP (port 21)
$ sudo ufw allow ftp
Allow SSH (port 22) From Specific IP
Let’s allow SSH connections only from IP address 10.230.21.30. Connections from other IP addresses will be blocked.
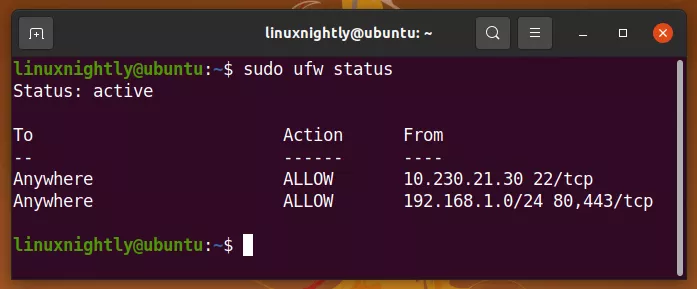
$ sudo ufw allow from 10.230.21.30 port ssh
Allow HTTP & HTTPS From Subnet
We can also allow connections to specific ports that are coming from a certain subnet. For example, let’s allow HTTP and HTTPS access to all IP addresses on the 192.168.1.0/24 subnet.
$ sudo ufw allow from 192.168.1.0/24 port 80,443 proto tcp
Delete Port From Ubuntu Firewall
1. If you need to delete one of the rules you added, first get a numbered output of all configured rules.
$ sudo ufw status numbered
Status: active
To Action From
-- ------ ----
[ 1] 22/tcp ALLOW IN Anywhere
[ 2] 80/tcp ALLOW IN Anywhere
[ 3] 22/tcp (v6) ALLOW IN Anywhere (v6)
[ 4] 80/tcp (v6) ALLOW IN Anywhere (v6)
If the firewall is inactive and you can’t see numbered rules, enable the firewall first.
$ sudo ufw enable
2. In our output, we have four rules configured. Let’s delete rule 1, which pertains to SSH.
$ sudo ufw delete 1 Deleting: allow 22/tcp Proceed with operation (y|n)? y Rule deleted
3. Usually, there will be two related rules – one for IPv4 and one for IPv6. Let’s make sure we delete both of them.
$ sudo ufw status numbered
Status: active
To Action From
-- ------ ----
[ 1] 80/tcp ALLOW IN Anywhere
[ 2] 22/tcp (v6) ALLOW IN Anywhere (v6)
[ 3] 80/tcp (v6) ALLOW IN Anywhere (v6)
As you can see, we need to delete number 2 to finish clearing the rules for SSH.
$ sudo ufw delete 2
4. You can also preface a ufw command with delete to undo an allow rule that you added earlier.
$ sudo ufw delete allow ssh Rule deleted Rule deleted (v6)
This will delete both the IPv4 rule and related IPv6 rule.
Delete All Firewall Rules
If you want to clear all the currently configured rules in ufw, you can use the reset option.
$ sudo ufw reset Resetting all rules to installed defaults. Proceed with operation (y|n)? y

